Cybersecurity analytics and the vital arterial pulse wave that flows through your network
By Jonathan Raymond, National Lead, Cybersecurity for SAS Canada
Before advances in technology permitted medical practitioners to monitor, record, visualize and predict cardiac outcomes through analysis of the arterial pulse wave, they could only refer to reactive data collected, typically, post-impact. Does that sound familiar?
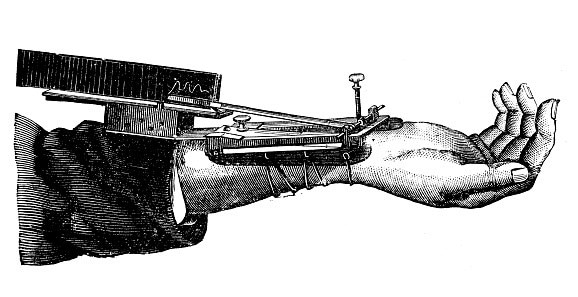
Technological advances, including the Sphygmograph in the graphic above, provided for a non-invasive means to gain critical insights from the velocity and volume of the arterial pulse. This allowed for significant scientific progress which continues to broaden our collective understanding of biology and physiology in a rapidly changing world.
Cybersecurity is at the same inflection point today. If you substitute the arterial pulse wave for your Network Flow Data and unique contextual data sources, you can appreciate how cybersecurity analytics can be a non-invasive means of gaining critical insights. The criticality in this case refers to the timing and accuracy of detecting threat activity at levels of fidelity beyond the reach of Security Information and Event Management (SIEM) and other traditional approaches. It ties to how timely insights can help your security practitioners respond sooner to more effectively mitigate the results of a cyber breach.
Cybersecurity today is complex .Our understanding of it remains limited at best. Much like early investigative approaches in medicine, Cybersecurity is a process of trial and error. There is a growing list of technologies and methodologies which are focused on recognizing and stopping known infections. They have essentially become the antibiotics of the cyber world. The trouble we all know is that “superbugs” grow unabated today. I can extend the analogy to insider threats and non-malware derived compromises, but you get the point.
The current state of cybersecurity, particularly the portion associated to preventative and detection frameworks, can be described as dire. Just refer to the near daily beat of highly publicized breaches reported in the press for confirmation.
Consider that;
* It takes on average over 200 days for a Canadian organization to detect a breach, and it’s often a third-party who raises the red flag, not the victim.
* The average breach costs Canadian organizations about $5 million, though many cost considerably more.
The challenges and associated pressure will continue to mount in Canada in 2016. According to the recent KPMG Cyber Watch Report, we will see 5 key trends affecting Canadian organizations this year:
- An increase in extortion-driven and ransomware incidents.
- Pressure to disclose breaches and threat responses in a timely manner will intensify.
- Widespread use of mobile devices and adoption of the Internet of Things (IoT) will bring a parallel increase in risk.
- Organizations will make greater use of real-time intelligence tools to monitor live attacks.
- Organizations will focus much more on risks posed by third-party vendors and suppliers.
Fortunately, Canadian companies are reacting to the changing landscape, according to a survey by consulting firm PricewaterhouseCooper. The survey found that half of Canadian enterprises now have a chief information security officer (CISO). Investment in cybersecurity rose 82 per cent year-over-year in 2015. A new coalition of Canadian banking, infrastructure and telecommunications companies, along with the Canadian Council of Chief Executives, has created the Canadian Cyber Threat Exchange (CCTX) to share information about threat activity. So there is reason to be optimistic. However, there remains considerable room for improvement.
One key area of significant promise continues to be the application of advanced analytics upon “big and fast” data. Today the application of advanced analytics has a proven track record in the Canadian financial services and insurance industries to predict, detect and minimize fraud and risk. Patterns of information and activity show the likelihood of a particular outcome. It works because a usable interface allows the people who understand the business—not just the data scientists—to manipulate the data and, among other things, develop processes to harden the system. In this case, the system is the financial operations of the FI. The same principle can be applied to the cyber security world. Experts agree that advanced behavioral analytics can be tuned to scale to the network and find anomalous activity at the device level moving up, down and across the network.
Advanced analytics applied properly can become a non-invasive way to detect anomalies in device usage and performance in near-real time, at scale. Imagine your complete network, security and business data combining to self-describe for you hourly the following insights;
- Which devices are not behaving like their peers,
- Which devices are not behaving like they used to,
- Which devices are showing indicators of breach activity we’ve seen before.
Through the continuous analysis of the arterial pulse wave of any sized network, cybersecurity analytics delivers critical and timely insights. The benefits include comprehensive and contextual situational awareness, better visualization and prioritization of threat mitigation efforts. The result is a game-changing and evolving augmentation to any programmatic cybersecurity optimization initiative.
As the National Lead for SAS Cybersecurity in Canada, Jonathan Raymond is responsible for business development and the go to market strategy for SAS’ Cybersecurity solution. With 15+ years in the Information (Cyber) Security industry, Jonathan has been a primary contributor upon the selling, design, deployment and ongoing management oversight and accountability for numerous high profile, complex and/or critical IT security projects within North America’s largest Financial Institutions, Oil and Gas, Electricity generation, transmission and distribution, Healthcare, Transportation, Retail, National Defense, and all levels of large Public Sector entities including law enforcement.
Read More
Get More Insights
Want more Insights from SAS? Subscribe to our Insights newsletter. Or check back often to get more insights on the topics you care about, including analytics, big data, data management, marketing, and risk & fraud.
